Tech
Resomee: Understanding the Concept Its Digital Relevance and Why People Are Searching for It

Introduction: Why Resomee Is Gaining Attention
The keyword resomee has recently started appearing more often in online searches, leaving many people curious about what it actually represents. At first glance, the word feels modern, clean, and tech-oriented, which naturally leads users to wonder whether it is a brand, a platform, a service, or a digital concept. In today’s internet-driven world, even a short and simple term can spark widespread interest if it appears in the right context.
From an expert standpoint, resomee fits perfectly into the pattern of emerging digital keywords. These are terms that gain visibility not through mass advertising, but through organic discovery—apps, websites, usernames, tools, or niche platforms. This article explores resomee in a clear, neutral, and informative way, focusing on how such keywords operate in the digital ecosystem, why they become searchable, and what users should realistically expect when encountering them.
What Is Resomee? A Clear and Practical Overview
Resomee is best understood as a modern digital term rather than a traditional dictionary word. It may represent a platform name, a project title, a brand identity, or a digital service that operates primarily online. The simplicity of the word is one of its strongest features, making it easy to remember and adaptable across different use cases.
In the digital space, names like resomee are often intentionally minimal. Short, brandable words are easier to market, easier to search, and easier to associate with innovation. Whether resomee is tied to professional tools, creative services, or online platforms, its structure suggests intentional design rather than randomness.
Experts often point out that such terms usually evolve over time. What starts as a niche name may grow into a recognizable identity depending on how it is used and adopted.
The Meaning Behind the Name “Resomee”
While resomee does not have a formal dictionary definition, its phonetic similarity to words like “resume” or “resonate” gives it an intuitive appeal. This type of naming strategy is common in digital branding, where emotional association matters more than literal meaning.
From an expert branding perspective, names that feel familiar without being direct copies tend to perform well. Resomee sounds professional, approachable, and modern, which makes it suitable for platforms related to careers, communication, creativity, or personal development.
Importantly, the lack of a rigid definition allows flexibility. Resomee can grow into whatever purpose it is assigned, without being limited by preconceived meanings.
Why Resomee Is Appearing in Search Results
Most users do not search for resomee randomly. They encounter it somewhere first—on a website, in a link, within an app interface, or through a mention on social media. Once seen, curiosity naturally leads to a search.
Experts refer to this as “context-driven search behavior.” When people see unfamiliar but intriguing terms, they search to understand relevance, legitimacy, and purpose. This behavior is extremely common with emerging digital platforms and tools.
Search engines then amplify this effect. As more people search for resomee, it becomes more visible, even to users who have never encountered it directly.
Resomee and Modern Digital Branding
In today’s crowded digital environment, branding is everything. Names like resomee reflect a shift away from long, descriptive titles toward short, versatile identities. This approach allows brands and platforms to expand without outgrowing their names.
From a branding expert’s view, resomee works well because it is neutral. It does not lock itself into one industry, language, or demographic. This flexibility makes it adaptable to global audiences and evolving markets.
Strong digital names also perform better in search engine optimization when paired with quality content. Over time, resomee can become associated with trust and authority if supported by consistent messaging and value.
Possible Use Cases Associated With Resomee
Although interpretations should remain neutral, resomee could logically be associated with several digital use cases. These might include professional tools, creative platforms, portfolio services, or communication-based solutions.
Experts emphasize that modern platforms often start small. A single function or niche audience can later expand into broader offerings. The name resomee allows for this type of organic growth.
What matters most is how the term is implemented. A strong user experience, transparency, and consistency will ultimately define what resomee represents to its audience.
User Curiosity and Digital Trust
One of the main reasons people search for resomee is trust. Users want to know whether a term they’ve encountered is legitimate, safe, and credible. This is a healthy and necessary habit in today’s digital landscape.
Experts recommend evaluating context before drawing conclusions. Where did you see resomee? Was it associated with a trusted platform or service? Did it appear in a professional or casual setting?
Trust is built gradually. Clear information, consistent presence, and positive user experiences all contribute to how a term like resomee is perceived over time.
The Role of Search Engines in Keyword Growth
Search engines play a major role in transforming obscure terms into searchable keywords. Once a term reaches a certain level of activity, it becomes part of suggestion lists, auto-complete features, and related searches.
This process often creates the illusion that a term is widely known, even if it is still niche. Experts describe this as algorithmic visibility rather than cultural popularity.
Resomee fits this pattern well. Its growing presence in search does not necessarily mean mass adoption, but it does indicate rising interest.
Common Misunderstandings About New Digital Terms
A frequent mistake is assuming that every unfamiliar keyword represents a major brand or product. In reality, many terms exist quietly within limited communities or early-stage projects.
Another misconception is assuming risk without evidence. While caution is important, not every unknown term is harmful or suspicious. Experts advise balancing curiosity with critical thinking.
Resomee, like many modern digital terms, should be approached with neutrality rather than assumption.
Digital Literacy and Responsible Interpretation
Understanding keywords like resomee requires digital literacy. This includes knowing how to evaluate sources, verify information, and recognize the difference between speculation and fact.
Experts stress that responsible interpretation benefits everyone. It reduces misinformation, builds healthier online ecosystems, and encourages more informed decision-making.
As users become more digitally aware, terms like resomee become less confusing and more contextualized.
How Resomee May Evolve Over Time
Digital identities are not static. Names, platforms, and tools evolve based on user needs, technology, and market conditions. Resomee may look very different in the future than it does today.
Experts often describe early-stage digital terms as “identity seeds.” With the right environment, they grow into recognizable brands. Without it, they may remain niche or fade away.
The key factor is value. If resomee consistently delivers something useful, meaningful, or innovative, it will naturally gain recognition.
The Bigger Picture Behind Resomee
Beyond the keyword itself, resomee represents a broader trend in how digital language evolves. Short, flexible, and brandable terms dominate modern naming conventions.
This trend reflects speed, scalability, and global accessibility. It also highlights how users interact with technology—through curiosity, search, and discovery.
Experts see this as a natural evolution of digital culture rather than a passing phase.
Conclusion: A Balanced and Informed View of Resomee
Resomee is best understood as a modern digital term that has gained attention through visibility and curiosity rather than hype. Its structure, naming style, and search behavior align with how contemporary platforms and tools emerge online.
An expert approach avoids speculation and focuses on context, usability, and credibility. Whether resomee becomes a widely recognized name or remains niche will depend on how it is developed and perceived over time.
For now, resomee stands as a clear example of how digital identity works in today’s internet landscape—quietly growing, shaped by user interest, and defined by the value it ultimately provides.
Tech
Vyxarind Qylorith: Exploring the Meaning Potential and Future of a Mysterious Digital Concept

introduction
In today’s rapidly evolving digital landscape, new terms, concepts, and identifiers appear constantly. One such intriguing term is vyxarind qylorith. At first glance, it may sound unfamiliar or even abstract, but that’s exactly what makes it interesting. Terms like this often emerge as part of experimental technologies, conceptual frameworks, or evolving digital ecosystems.
Whether vyxarind qylorith represents a system identifier, a conceptual framework, or a symbolic name for a digital process, it highlights an important reality: modern technology is constantly expanding beyond traditional definitions. New naming conventions, unique identifiers, and symbolic terms are shaping how we understand digital architecture.
In this article, we’ll explore the possible meanings, applications, and importance of vyxarind qylorith. We’ll also examine how it reflects broader trends in technology, innovation, and digital transformation.
Understanding the Concept Behind Vyxarind Qylorith
To understand vyxarind qylorith, it’s important to first recognize how modern systems use abstract naming conventions. Technology often relies on unique identifiers, symbolic labels, and conceptual names to represent processes, systems, or digital entities. These names may not always have a literal meaning but serve a functional or structural purpose.
Vyxarind qylorith can be seen as a representation of a unique digital element. It may function as an identifier, a project name, or even a conceptual label used in experimental or developmental environments. These kinds of terms help distinguish one system component from another.
Another way to view vyxarind qylorith is as a symbolic representation of innovation. Many new technologies begin with abstract names before they become widely recognized. These names help developers organize their work and create structured digital environments.
It also reflects the increasing complexity of digital ecosystems. As systems grow more advanced, they require more unique identifiers and conceptual labels. Terms like vyxarind qylorith help maintain organization and clarity within these environments.
The Role of Unique Naming in Modern Technology
Unique naming plays a critical role in modern technology. Without distinct names and identifiers, managing digital systems would be extremely difficult. Every component, process, and resource needs a clear identity to function efficiently.
Vyxarind qylorith could represent a system identifier used to track specific processes or data points. This ensures that each element can be located, modified, or managed without confusion. Unique identifiers improve system reliability and performance.
Naming conventions also improve communication among developers and engineers. When systems have clear and unique names, teams can collaborate more effectively. This reduces errors and improves workflow efficiency.
Additionally, unique names help support automation. Automated systems rely on identifiers to perform tasks without human intervention. This increases speed and reduces the risk of human error.
As technology continues to evolve, the importance of unique naming will only increase. Terms like vyxarind qylorith represent this growing need for precise digital identification.
Possible Applications of Vyxarind Qylorith in Digital Systems
Vyxarind qylorith could have several potential applications depending on its intended purpose. One possible use is as a database identifier. Databases rely on unique identifiers to track records and maintain organization. This ensures accurate data retrieval and management.
Another possible application is in cybersecurity. Unique identifiers are often used to manage authentication, encryption, and secure communications. Vyxarind qylorith could represent a security token, encryption key, or access identifier.
It may also function as a project or system label. Developers often use unique names to identify projects, modules, or experimental features. This helps organize development and track progress.
Cloud computing is another area where such identifiers are essential. Cloud platforms manage massive amounts of data and resources. Unique identifiers ensure that each resource can be managed efficiently.
Even artificial intelligence systems rely on identifiers to manage data and processes. Vyxarind qylorith could represent a model, dataset, or operational component within an AI system.
How Vyxarind Qylorith Reflects Digital Innovation
Digital innovation often involves creating new systems, frameworks, and processes. New names and identifiers naturally emerge as part of this process. Vyxarind qylorith reflects the creative and experimental nature of technological development.
Innovation requires flexibility and adaptability. Abstract names allow developers to create new concepts without being restricted by traditional naming conventions. This encourages creativity and experimentation.
It also reflects the transition from human-centered naming to machine-centered naming. Machines process identifiers differently than humans. Unique combinations of letters and numbers improve efficiency and accuracy.
Another important aspect is scalability. As systems grow, they require more identifiers. Abstract naming conventions help support large-scale digital environments.
Vyxarind qylorith represents this shift toward more advanced and flexible digital systems.
The Importance of Structure and Organization in Digital Environments
Digital systems rely heavily on structure and organization. Without proper structure, systems would become chaotic and inefficient. Identifiers like vyxarind qylorith help maintain order.
Organization improves system performance. When systems can locate resources quickly, they operate more efficiently. This improves user experience and reduces processing time.
Structure also improves reliability. Systems with clear organization are less likely to experience errors or failures. Identifiers ensure that each component is correctly managed.
Another benefit is maintainability. Developers can easily update and manage systems when components have clear identifiers. This improves long-term system stability.
As digital environments continue to grow, structure and organization will remain essential.
Security Implications of Unique Digital Identifiers
Security is one of the most important aspects of modern technology. Unique identifiers play a key role in protecting systems and data. Vyxarind qylorith could represent a secure identifier used to protect digital resources.
Identifiers help verify identity and control access. This prevents unauthorized users from accessing sensitive information. Security systems rely heavily on unique identifiers.
Encryption systems also use identifiers to manage keys and protect communications. This ensures data confidentiality and integrity.
Another important role is activity tracking. Identifiers allow systems to monitor activity and detect suspicious behavior. This improves security and helps prevent attacks.
Unique identifiers strengthen overall system security and reliability.
The Future Potential of Concepts Like Vyxarind Qylorith
As technology continues to evolve, concepts like vyxarind qylorith will become more common. Digital systems will require more identifiers to manage increasing complexity.
Artificial intelligence will rely heavily on identifiers to manage data and processes. This will enable more advanced capabilities and automation.
Cloud computing will continue to expand. Unique identifiers will ensure efficient resource management and scalability.
Cybersecurity will also depend on advanced identifiers to protect systems from evolving threats.
Even emerging technologies like virtual reality and blockchain will rely on unique identifiers to function effectively.
Vyxarind qylorith represents the future of digital organization and innovation.
Why Understanding Digital Identifiers Matters
Understanding digital identifiers helps you better understand how technology works. Identifiers are essential for organization, security, and efficiency.
They allow systems to manage data accurately and reliably. This improves performance and user experience.
They also support automation and advanced technologies. Without identifiers, modern systems would not function effectively.
Understanding these concepts can help students, developers, and technology enthusiasts gain deeper insight into digital systems.
Vyxarind qylorith represents a small but important part of this larger technological framework.
Conclusion: The Symbolic and Practical Importance of Vyxarind Qylorith
Vyxarind qylorith may appear mysterious at first, but it represents an important concept in modern technology. Unique identifiers and abstract naming conventions play a critical role in digital systems.
They improve organization, efficiency, security, and scalability. They support innovation and enable advanced technologies.
As digital systems continue to evolve, identifiers like vyxarind qylorith will become even more important. They will help maintain structure and support future technological advancements.
Understanding these concepts provides valuable insight into how modern technology functions. It reveals the hidden systems that keep digital environments running smoothly.
Tech
567gk3: Understanding Its Meaning Uses and Why It Matters in Today’s Digital World
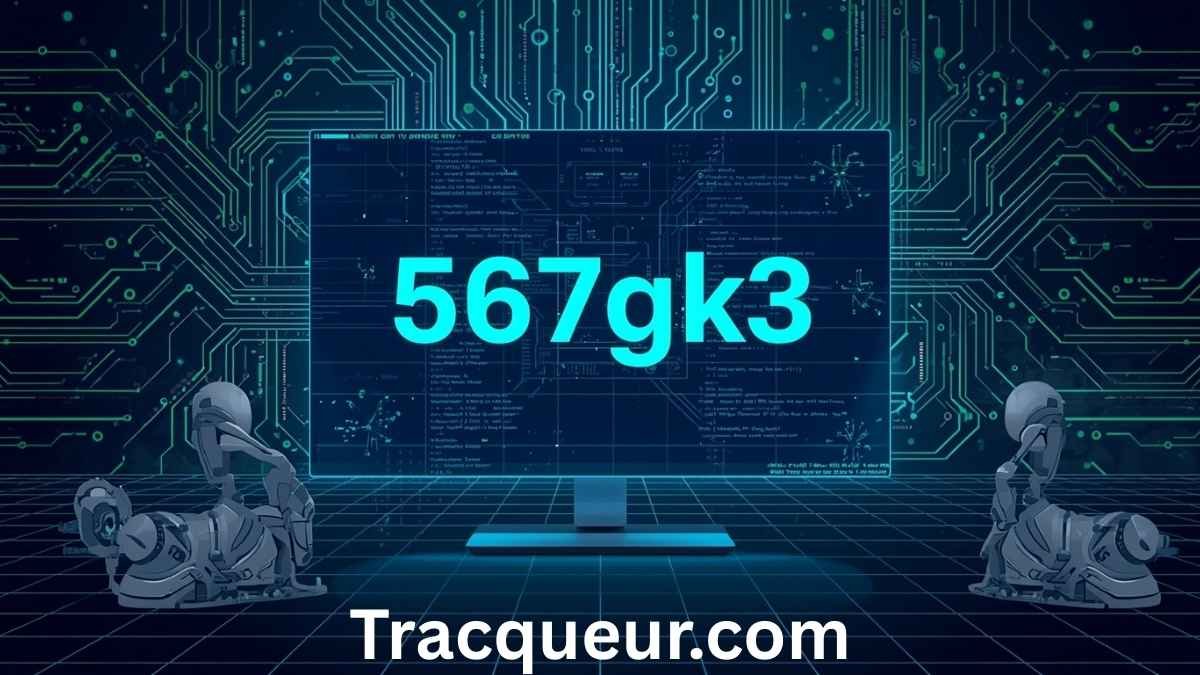
Introduction
In today’s fast-moving digital environment, unusual codes and identifiers like 567gk3 often appear in technical systems, online platforms, and digital workflows. While at first glance it may look like a random combination of numbers and letters, codes such as 567gk3 typically serve a specific purpose. They help systems identify, organize, and secure information in ways that humans alone cannot manage efficiently.
Whether you’re a student, developer, digital marketer, or just someone curious about technology, understanding identifiers like 567gk3 can give you deeper insight into how modern systems function behind the scenes. These codes play an essential role in maintaining structure, accuracy, and security across digital environments.
In this article, we’ll explore what 567gk3 represents, where it might be used, why it matters, and how it reflects the broader trends shaping today’s technology landscape.
What Is 567gk3 and Why Does It Exist?
At its core, 567gk3 represents what’s commonly known as a unique identifier. Unique identifiers are special codes assigned to specific items, users, or processes so systems can recognize and track them without confusion. These identifiers prevent errors and ensure smooth operations across complex digital platforms.
Imagine a system managing millions of users, files, or transactions. Using names alone would create conflicts because multiple items can share similar names. A code like 567gk3 eliminates this problem by acting as a one-of-a-kind reference. No two records share the same identifier, which ensures precision.
Another important reason identifiers like 567gk3 exist is automation. Modern systems rely heavily on automation to process tasks quickly. Machines can process codes faster and more reliably than human-readable labels. This improves speed, accuracy, and overall system performance.
In many cases, identifiers like 567gk3 are generated automatically by software. This means users don’t have to create or manage them manually. The system assigns them behind the scenes, allowing users to focus on their actual tasks rather than worrying about technical organization.
Common Places Where 567gk3-Style Codes Are Used
Identifiers similar to 567gk3 appear in many areas of technology, even if users don’t always notice them. One of the most common uses is in databases. Every record in a database often has a unique code that distinguishes it from others. This allows systems to retrieve and update information quickly.
Another common use is in web applications. When you sign up for a service, upload a file, or complete a transaction, the system assigns a unique identifier. This identifier helps the platform track your activity securely and efficiently.
Product tracking is another major example. Online stores use identifiers to manage inventory, orders, and shipments. Instead of relying on product names alone, they assign unique codes. This reduces errors and ensures accurate processing.
Identifiers like 567gk3 also appear in security systems. Authentication tokens, session IDs, and encrypted keys often use similar formats. These codes help verify identity and protect sensitive information from unauthorized access.
Even software development relies heavily on identifiers. Developers use them to track bugs, manage features, and organize code efficiently. Without identifiers, managing complex software projects would be nearly impossible.
How 567gk3 Improves Organization and Efficiency
One of the biggest benefits of identifiers like 567gk3 is improved organization. Digital systems handle enormous amounts of information. Without proper identification, data would quickly become disorganized and difficult to manage.
Unique identifiers make it easy to locate specific records instantly. Instead of searching through thousands or millions of entries, the system can find the exact match using the identifier. This saves time and reduces system load.
Another key advantage is accuracy. Human-readable labels can be duplicated or misspelled. Identifiers like 567gk3 eliminate this risk because they are designed to be unique. This ensures that the correct data is always accessed and modified.
Efficiency is also greatly improved. Systems can process identifiers faster than complex descriptions. This leads to faster loading times, smoother performance, and better overall user experience.
In large organizations, identifiers are essential for scalability. As systems grow, identifiers allow them to manage increasing amounts of data without losing structure or performance.
The Role of 567gk3 in Digital Security
Security is one of the most important aspects of modern technology, and identifiers like 567gk3 play a critical role in protecting systems and users. Many security mechanisms rely on unique codes to verify identity and prevent unauthorized access.
For example, session identifiers allow systems to recognize users after login. Instead of requiring constant authentication, the system uses the session ID to maintain secure communication. This improves both security and convenience.
Encryption systems also use identifiers to manage keys and protect sensitive data. These identifiers ensure that only authorized users and systems can access protected information.
Another important role is preventing conflicts and fraud. Unique identifiers make it difficult for malicious actors to duplicate or manipulate records. This strengthens system integrity and reduces security risks.
Additionally, identifiers help track system activity. If a problem occurs, administrators can use identifiers to trace the issue and resolve it quickly. This improves system reliability and safety.
Why Codes Like 567gk3 Are Becoming More Important
As technology continues to evolve, identifiers like 567gk3 are becoming increasingly important. Modern systems handle more data than ever before. Without proper identification, managing this data would be impossible.
Cloud computing is one major reason identifiers are essential. Cloud platforms manage massive amounts of distributed data. Unique identifiers ensure accurate tracking and retrieval across different servers and locations.
Artificial intelligence and machine learning also rely heavily on identifiers. These systems process large datasets and require precise identification to function correctly.
Another reason is the growth of online services. From social media to e-commerce, digital platforms rely on identifiers to manage users, content, and transactions efficiently.
Even emerging technologies like blockchain depend on unique identifiers. Blockchain uses cryptographic identifiers to ensure transparency, security, and trust.
As digital systems become more complex, identifiers like 567gk3 will continue to play a central role in maintaining order and functionality.
How Identifiers Like 567gk3 Are Generated
Most identifiers are generated automatically using algorithms. These algorithms ensure that each identifier is unique and does not conflict with existing ones.
One common method is sequential generation. The system assigns identifiers in order, such as increasing numbers combined with letters. This method is simple and effective for many applications.
Another method is random generation. Random identifiers are harder to predict, which improves security. This approach is commonly used in authentication and encryption systems.
Some systems use hybrid methods that combine sequential and random elements. This provides both organization and security.
Advanced systems may use cryptographic techniques to generate identifiers. These identifiers are extremely secure and difficult to duplicate or manipulate.
The exact method depends on the system’s requirements, but the goal is always the same: create unique, reliable identifiers.
The Future of Digital Identifiers Like 567gk3
The future of digital identifiers is closely tied to the future of technology itself. As systems become more advanced, identifiers will become even more important.
One trend is increased use of secure identifiers. Security threats are constantly evolving, and identifiers will play a key role in protecting systems and data.
Another trend is global integration. Identifiers will help connect systems across different platforms and organizations. This will improve efficiency and enable new digital services.
Automation will also increase reliance on identifiers. Automated systems need precise identification to function correctly.
Artificial intelligence will use identifiers to manage complex data relationships. This will improve accuracy and enable more advanced capabilities.
As digital transformation continues, identifiers like 567gk3 will remain a fundamental part of modern technology.
Conclusion: Why 567gk3 Represents More Than Just a Code
Although 567gk3 may look like a simple combination of characters, it represents a powerful concept that supports modern digital systems. Unique identifiers are essential for organization, efficiency, security, and scalability.
They allow systems to manage massive amounts of data accurately and efficiently. They protect users and information from security threats. They enable automation and support advanced technologies like cloud computing and artificial intelligence.
Understanding identifiers like 567gk3 provides valuable insight into how digital systems work behind the scenes. These codes may not always be visible, but they are essential for keeping modern technology running smoothly.
As technology continues to evolve, identifiers will become even more important. They will remain a key foundation of digital infrastructure, ensuring that systems remain organized, secure, and efficient.
Tech
860-553-3468: A Practical Guide to Understanding Unknown Phone Numbers Today

Introduction
Seeing an unfamiliar phone number like 860-553-3468 pop up on your screen can instantly trigger curiosity or concern. In a world where phone calls are no longer limited to friends and family, it’s normal to pause and wonder who might be on the other end of the line. Missed calls from unknown numbers are now part of everyday digital life.
With the growth of automated dialing systems, virtual phone services, and remote communication tools, phone numbers no longer tell a simple story. A number such as 860-553-3468 could represent a legitimate business call, an automated notification, or something that simply requires a bit more investigation.
This article takes an expert yet relaxed approach to understanding numbers like 860-553-3468. Instead of jumping to conclusions, we’ll explore how these numbers work, why they appear, and how to respond thoughtfully and confidently.
Breaking Down the Area Code and Number Format
The phone number 860-553-3468 begins with the 860 area code, which is traditionally associated with the state of Connecticut. Area codes were originally designed to reflect geographic regions, helping route calls efficiently across the country.
However, modern telecommunications have changed how area codes function. Today, a number with an 860 area code does not guarantee that the caller is physically located in Connecticut. Virtual phone services allow individuals and businesses to use numbers from specific regions regardless of their actual location.
Understanding this context is important. The structure of 860-553-3468 offers a clue, not a conclusion. Treating area codes as informational rather than definitive helps users avoid unnecessary assumptions about who is calling and why.
Common Reasons You Might See 860-553-3468
There are several legitimate reasons why 860-553-3468 might appear on your phone. It could be a return call from a business you contacted earlier, a reminder from a service provider, or an automated system delivering an update or confirmation.
Many organizations rely on outbound calling systems to manage communication efficiently. These systems often use numbers that don’t immediately match a company’s public-facing contact information, which can make calls feel unfamiliar even when they are legitimate.
Of course, not every unknown call requires immediate action. The key is recognizing that unfamiliar does not automatically mean unsafe. Numbers like 860-553-3468 are part of a much larger and more complex communication ecosystem.
How to Assess an Unknown Call Calmly and Safely
When dealing with an unfamiliar number such as 860-553-3468, the first step is to stay calm and observant. Did the caller leave a voicemail? Was there a clear reason given for the call? Legitimate callers usually provide some form of context.
Another factor to consider is frequency. A single missed call is often harmless, while repeated calls without explanation may deserve closer attention. Patterns matter more than isolated events when evaluating unknown numbers.
Most importantly, avoid sharing personal or sensitive information unless you are confident about the caller’s identity. A phone number alone does not establish trust. Taking a moment to evaluate before responding can prevent unnecessary stress or risk.
The Role of Online Searches and Shared Experiences
Many people search numbers like 860-553-3468 online to see if others have reported similar calls. This behavior reflects a growing awareness of digital safety and a desire to make informed decisions based on shared experiences.
Online discussions can sometimes reveal useful patterns, such as whether a number is frequently reported or associated with a particular type of call. While this information can be helpful, it should be viewed as guidance rather than absolute truth.
Not all online claims are accurate, and context matters. Use online search results as one piece of the puzzle, not the final answer. Balanced judgment always leads to better decisions than relying on a single source.
Managing Unknown Numbers with Modern Tools
Smartphones now offer several built-in tools to help manage unknown calls more effectively. Features like call screening, voicemail transcription, and silence unknown callers allow users to stay informed without being constantly interrupted.
Blocking a number like 860-553-3468 is an option if calls become persistent or disruptive. Blocking doesn’t identify the caller, but it does give users control over their communication experience.
At the same time, moderation is important. Automatically blocking every unfamiliar number can lead to missed opportunities or important information. The goal is not avoidance, but smart and intentional call management.
Why Awareness Is Better Than Assumption
One of the biggest challenges with unknown phone numbers is the tendency to assume the worst. While caution is healthy, assumptions often lead to unnecessary anxiety. Numbers like 860-553-3468 exist within a neutral system until context is provided.
Understanding how modern phone systems operate helps replace fear with clarity. Automated calls, virtual numbers, and remote work have changed how communication looks, but not every change is negative.
By focusing on awareness rather than assumption, users can navigate unknown calls with confidence. Knowledge creates calm, and calm leads to better decisions.
Final Thoughts on 860-553-3468
From an expert standpoint, 860-553-3468 should be viewed as a data point, not a judgment. Without context, a phone number is simply a tool used within a complex communication network.
The smartest approach is a balanced one. Stay observant, use available tools, and avoid reacting emotionally to unfamiliar calls. Most communication scenarios resolve themselves with patience and clarity.
In a world where digital communication continues to evolve, learning how to handle unknown numbers like 860-553-3468 is an essential skill. With the right mindset and awareness, you can stay informed, protected, and in control.
-

 Entertainment3 days ago
Entertainment3 days agoFakboitv: Exploring the Digital Identity Behind a Rising Online Brand
-
General7 days ago
Do Government Grants Cover Heat Pump Installation?
-

 Beauty & Skincare1 week ago
Beauty & Skincare1 week agoSerumcu: Understanding the Term Its Uses and Its Growing Relevance
-

 General1 week ago
General1 week agoRolerek: Meaning Usage and Its Place in Modern Digital Culture
-

 Entertainment1 week ago
Entertainment1 week agoNinewin: Understanding the Platform Digital Appeal and User Experience
-

 Food1 week ago
Food1 week agoBjudlunch: A Simple Guide to Sweden’s Most Thoughtful Lunch Tradition
-

 General5 days ago
General5 days agoOrdenari: Redefining Structure Simplicity and Smart Organization in the Modern World
-

 Entertainment5 days ago
Entertainment5 days agoTabootune: Redefining Bold Expression in the Digital Sound Era





